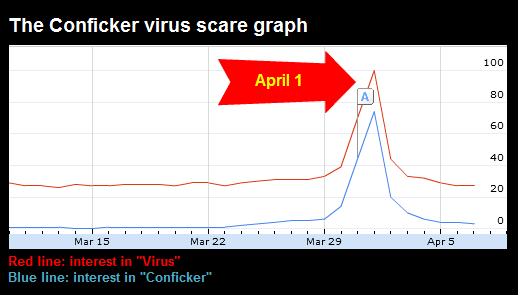
In response to growing concerns from the public and the media about the possible threat that may be unleashed by the Conficker worm on April 1st, McAfee, Inc. (NYSE: MFE), the leading Internet security company, today took steps to allay fears and offer some simple guidelines for consumers and businesses to ensure they are fully protected.
What is the Conficker worm?
Conficker first surfaced late last year, taking advantage of a security flaw in Microsoft’s Windows operating system to spread itself. Microsoft provided an emergency fix for the vulnerability last October with Security Update MS08-067. However, because many systems were not patched or properly protected with security software, Conficker has slithered onto as many as 12 million Windows computers, according to some estimates.
Some experts believe that one variant of the worm, Conficker.C, may activate on April 1 and start another assault on Windows computers. Computers infected with Conficker become part of an army of compromised computers and could be used to launch attacks on Web sites, distribute spam, host phishing Web sites or other criminal activities. Additionally, once it is on a computer, Conficker digs itself in by attempting to deactivate security software and sabotaging tools to remove it.
How do I know if I’m affected?
“One of the symptoms of this worm is that it blocks access to Web sites of Internet security companies,” says Dave Marcus, of McAfee Avert Labs. “A pretty good indication of whether your computer has been infected is to try and visit McAfee’s Web site: www.mcafee.com. If the site won’t load, you will need to clean your infected computer by searching for McAfee® Avert® Labs Stinger tool on the Internet. You should also install Microsoft’s patch to prevent the worm from reinstalling itself.”
As Conficker blocks popular security Web sites, including www.mcafee.com, users should search for “stinger virus removal” on the Internet, if they are unable to obtain it from McAfee’s Web site. Alternatively, users may transport the Stinger tool via a USB stick from an uninfected computer.
McAfee has released a free tool that will help assess multiple computers for the presence of Conficker. This new tool, termed ConTest, may be downloaded at no charge at http://www.mcafee.com/us/enterprise/confickertest.html.
Removing Conficker and preventing re-infection
Anti-malware solutions will clean the infection and use behavioral detections techniques like buffer overflow protection to prevent future infections. This is important because Conficker can propagate via portable media such as an infected USB drive. As the drive is accessed, the system processes autorun.inf and executes the attack. And finally, ensure all computers have Microsoft Security Update MS08-067 installed.
For more information on the Conficker worm and how users can protect themselves, visit http://www.mcafee.com/us/threat_center/conficker.html.
McAfee, Inc., headquartered in Santa Clara, California, is the world's largest dedicated security technology company. McAfee is relentlessly committed to tackling the world's toughest security challenges. The company delivers proactive and proven solutions and services that help secure systems and networks around the world, allowing users to safely connect to the Internet, browse and shop the web more securely. Backed by an award-winning research team, McAfee creates innovative products that empower home users, businesses, the public sector and service providers by enabling them to prove compliance with regulations, protect data, prevent disruptions, identify vulnerabilities, and continuously monitor and improve their security. http://www.mcafee.com